Fail2Ban 对接NGINX 防暴力破解!
Fail2Ban 是一个广泛使用的工具,用于检测恶意登录尝试和其他异常活动,并自动封锁攻击者的IP地址。您可以配置它来检测过多的连接请求,然后暂时封锁来自恶意IP地址的访问。
安装与启动
Debian/Ubuntu安装
apt update -y && apt install -y fail2banCentOS安装
yum update -y
yum install -y epel-release
yum install -y fail2ban
yum install -y nano启动
systemctl start fail2ban开机自启
systemctl enable fail2ban查看状态
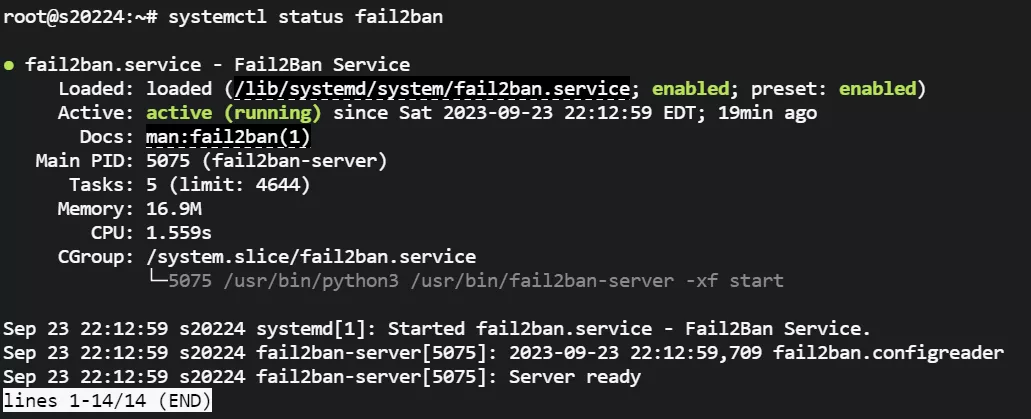
systemctl status fail2ban主配置文件
主配置文件创建本地副本
cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local编辑本地副本
nano /etc/fail2ban/jail.local重启服务
systemctl restart fail2banSSH防御 防止暴力破解
rm -rf /etc/fail2ban/jail.d/*
nano /etc/fail2ban/jail.d/sshd.local插入以下文本
[sshd]
enabled = true
mode = normal
backend = systemd重启服务
systemctl restart fail2ban查看封锁列表
fail2ban-client status查看SSH封锁情况
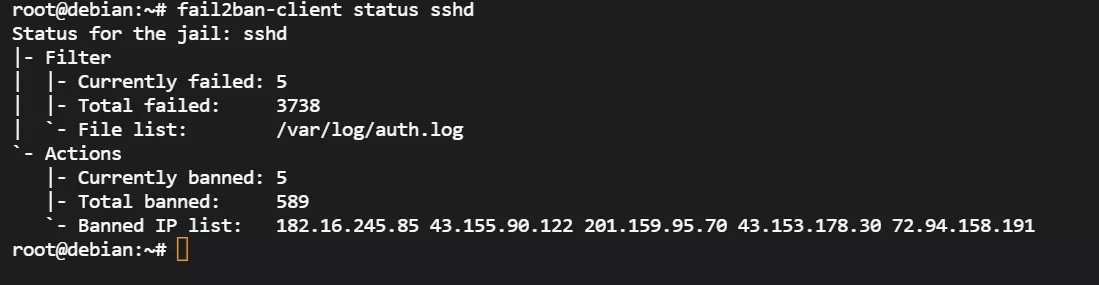
fail2ban-client status sshd网站防御
采用科技lion的LDNMP建站方案可以使用该防御
删除之前nginx容器
docker rm -f nginx部署新容器我们把log映射出来
docker run -d --name nginx --restart always --network web_default -p 80:80 -p 443:443 -v /home/web/conf.d:/etc/nginx/conf.d -v /home/web/certs:/etc/nginx/certs -v /home/web/html:/var/www/html **-v /home/web/log/nginx:/var/log/nginx** nginx创建网站拦截规则
nano /etc/fail2ban/jail.d/nginx.local插入规则
[nginx-http-auth]
enabled = true
mode = fallback
port = http,https
logpath = /home/web/log/nginx/access.log
[nginx-limit-req]
enabled = true
port = http,https
logpath = /home/web/log/nginx/access.log
[nginx-botsearch]
enabled = true
port = http,https
logpath = /home/web/log/nginx/access.log
[nginx-bad-request]
enabled = true
port = http,https
logpath = /home/web/log/nginx/access.log
[php-url-fopen]
enabled = true
port = http,https
logpath = /home/web/log/nginx/access.log重启服务
systemctl restart fail2ban查看nginx封锁情况
fail2ban-client status nginx-http-auth查看总日志
tail -f /var/log/fail2ban.log卸载
systemctl disable fail2ban
systemctl stop fail2ban
apt remove -y --purge fail2ban
find / -name "fail2ban" -type d
rm -rf /etc/fail2ban